Undermine Defense Mac OS
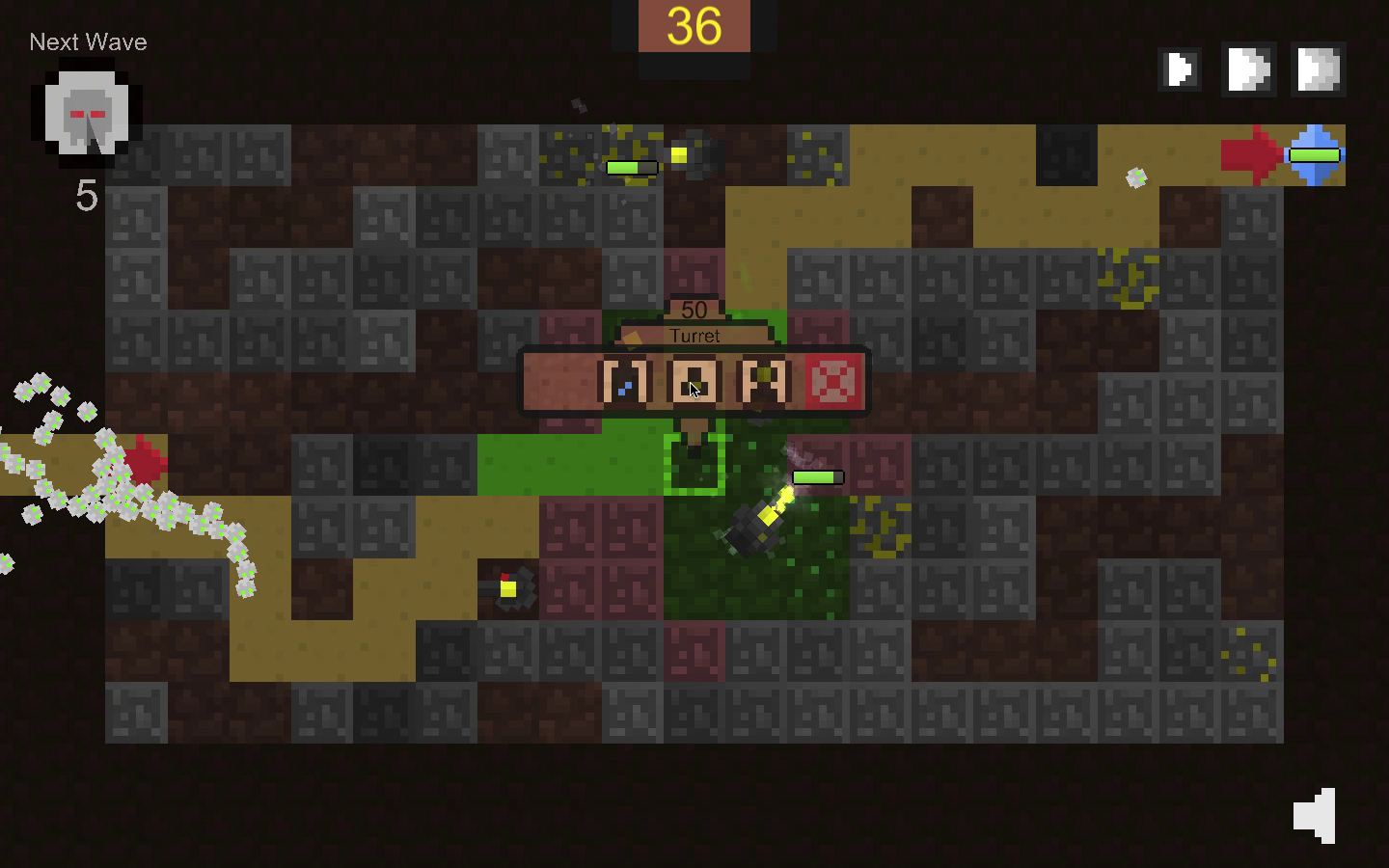
Fight with hordes of enemies in procedural maps while mining for resources.
- Undermine Defense Mac Os 11
- Undermine Defense Mac Os Download
- Undermine Defense Mac Os Catalina
- Undermine Defense Mac Os X
OS X, files, accounts, programs etc., will be gone. This is unfortunately necessary to remove all the little hidden caches, log files, databases and files squirreled around on the partition. 4: Quit and reinstall OS X using your AppleID and password, you will need to be on a fast and reliable Internet connection.
Features
- Procedural maps
- Online leaderboard
- Cool particle fx!
- Not so cool sound fx! ( But at least there is one)
- 4 different enemy types
- 3 different turrets with upgrades
- Installation Instructions for Mac OS X 10.6 (Snow Leopard) and Below. The Smartcard Services software is already included in OS X 10.6 (Snow Leopard) and below. However, the SystemCACertificates Keychain may still need to be loaded into Keychain Access. To ensure this has been done, please follow these instructions.
- UnderMine.v1.0.0.52.MacOS.zi p (170.45 MB) Choose free or premium download SLOW DOWNLOAD. FAST INSTANT DOWNLOAD.
- This makes it safer from surveillance than proprietary software (like Windows or Mac OS). To defend your freedom as well as protect yourself from surveillance, we recommend you switch to a free software operating system like GNU/Linux. Learn more about free software at fsf.org.
Criteria I used:
Strategy (Used)Tower Defense (Used)- Short-term Memory (Didn't had enough time)
Energy Drink (Used but as a energy giving turret called 'Dispenser turret')Playability (Used)
Web version will come out once the jam is over
This game and all of it's assets are made in 96 hours for #JamDna 3.
@Wolderado
I had so much fun making it. I hope the game can grow beyond this prototype state
| Status | Released |
| Platforms | Windows, macOS, Linux, HTML5 |
| Rating | |
| Author | Wolderado |
| Genre | Strategy |
| Made with | Unity |
| Tags | 2D, 8-Bit, defense, horde, Pixel Art, Tower Defense |
Download
Click download now to get access to the following files:
Development log
- Update 1.2.0 (New Enemy, New Turret, and a New Event!) with lots of gifs!Jun 21, 2020
Undermine Defense Mac Os 11
Log in with itch.io to leave a comment.
Amazing tower defense! Amazing sounds and graphics! I kill 3000+ enemies :)
NOTE: This guide is not being actively reviewed or updated, and is currently retired. If you would like to use Adium or another form of OTR messaging for macOS, please refer to those services’ websites and documentation for information on how to install and use them.
Adium is a free and open source instant messaging client for OS X that allows you to chat with individuals across multiple chat protocols, including Google Hangouts, Yahoo! Messenger, Windows Live Messenger, AIM, ICQ, and XMPP.
OTR (Off-the-record) is a protocol that allows people to have confidential conversations using the messaging tools they’re already familiar with. This should not be confused with Google's “Off the record,” which merely disables chat logging, and does not have encryption or verification capabilities. For Mac users, OTR comes built-in with the Adium client.
OTR employs end-to-end encryption. This means that you can use it to have conversations over services like Google Hangouts without those companies ever having access to the contents of the conversations. However, the fact that you are having a conversation is visible to the provider.
Why Should I Use Adium + OTR? Anchor link
When you have a chat conversation using Google Hangouts on the Google website, that chat is encrypted using HTTPS, which means the content of your chat is protected from hackers and other third parties while it’s in transit. It is not, however, protected from Google, which have the keys to your conversations and can hand them over to authorities or use them for marketing purposes.
After you have installed Adium, you can sign in to it using multiple accounts at the same time. For example, you could use Google Hangouts and XMPP simultaneously. Adium also allows you to chat using these tools without OTR. Since OTR only works if both people are using it, this means that even if the other person does not have it installed, you can still chat with them using Adium.
Adium also allows you to do out-of-band verification to make sure that you’re talking to the person you think you’re talking to and you are not being subject to a man-in-the-middle attack. For every conversation, there is an option that will show you the key fingerprints it has for you and the person with whom you are chatting. A 'key fingerprint' is a string of characters like '342e 2309 bd20 0912 ff10 6c63 2192 1928,” that’s used to verify a longer public key. Exchange your fingerprints through another communications channel, such as Twitter DM or email, to make sure that no one is interfering with your conversation. If the keys don't match, you can't be sure you're talking to the right person. In practice, people often use multiple keys, or lose and have to recreate new keys, so don't be surprised if you have to re-check your keys with your friends occasionally.
Limitations: When Should I Not Use Adium + OTR? Anchor link
Technologists have a term to describe when a program or technology might be vulnerable to external attack: they say it has a large “attack surface.” Adium has a large attack surface. It is a complex program, which has not been written with security as a top priority. It almost certainly has bugs, some of which might be used by governments or even big companies to break into computers that are using it. Using Adium to encrypt your conversations is a great defense against the kind of untargeted dragnet surveillance that is used to spy on everyone's Internet conversations, but if you think you will be personally targeted by a well-resourced attacker (like a nation-state), you should consider stronger precautions, such as PGP-encrypted email.
Installing Adium + OTR On Your Mac Anchor link
Step 1: Install the program
First, go to https://adium.im/ in your browser. Choose “Download Adium 1.5.9.” The file will download as a .dmg, or disk image, and will probably be saved to your “downloads” folder.
Double-click on the file; that will open up a window that looks like this:
Move the Adium icon into the “Applications” folder to install the program. Once the program is installed, look for it in your Applications folder and double-click to open it.
Step 2: Set up your account(s)
First, you will need to decide what chat tools or protocols you want to use with Adium. The setup process is similar, but not identical, for each type of tool. You will need to know your account name for each tool or protocol, as well as your password for each account.
To set up an account, go to the Adium menu at the top of your screen and click “Adium” and then “Preferences.” This will open a window with another menu at the top. Select “Accounts,” then click the “+” sign at the bottom of the window. You will see a menu that looks like this:
Select the program that you wish to sign in to. From here, you will be prompted either to enter your username and password, or to use Adium’s authorization tool to sign in to your account. Follow Adium’s instructions carefully.
How to Initiate an OTR Chat Anchor link
Undermine Defense Mac Os Download
Once you have signed in to one or more of your accounts, you can start using OTR.
Remember: In order to have a conversation using OTR, both people need to be using a chat program that supports OTR.
Undermine Defense Mac Os Catalina
Step 1: Initiate an OTR Chat
First, identify someone who is using OTR, and initiate a conversation with them in Adium by double-clicking on their name. Once you have opened the chat window, you will see a small, open lock in the upper left-hand corner of the chat window. Click on the lock and select “Initiate Encrypted OTR Chat.”
Step 2: Verify Your Connection
Once you have initiated the chat and the other person has accepted the invitation, you will see the lock icon close; this is how you know that your chat is now encrypted (congratulations!) – But wait, there’s still another step!
At this time, you have initiated an unverified, encrypted chat. This means that while your communications are encrypted, you have not yet determined and verified the identity of the person you are chatting with. Unless you are in the same room and can see each other’s screens, it is important that you verify each other’s identities. For more information, read the module on Key Verification.
Undermine Defense Mac Os X
To verify another user’s identity using Adium, click again on the lock, and select “Verify.” You will be shown a window that displays both your key and the key of the other user. Some versions of Adium only support manual fingerprint verification. This means that, using some method, you and the person with whom you’re chatting will need to check to make sure that the keys that you are being shown by Adium match precisely.
The easiest way to do this is to read them aloud to one another in person, but that’s not always possible. There are different ways to accomplish this with varying degrees of trustworthiness. For example, you can read your keys aloud to one another on the phone if you recognize each other’s voices or send them using another verified method of communication such as PGP. Some people publicize their key on their website, Twitter account, or business card.
The most important thing is that you verify that every single letter and digit matches perfectly.
Step 3: Disable Logging
Now that you have initiated an encrypted chat and verified your chat partner’s identity, there’s one more thing you need to do. Unfortunately, Adium logs your OTR-encrypted chats by default, saving them to your hard drive. This means that, despite the fact that they’re encrypted, they are being saved in plain text on your hard drive.
To disable logging, click “Adium” in the menu at the top of your screen, then “Preferences.” In the new window, select “General” and then disable “Log messages” and “Log OTR-secured chats.” Remember, though, that you do not have control over the person with whom you are chatting—she could be logging or taking screenshots of your conversation, even if you yourself have disabled logging.
Your settings should now look like this: